Container Utilization Source Mapping Import
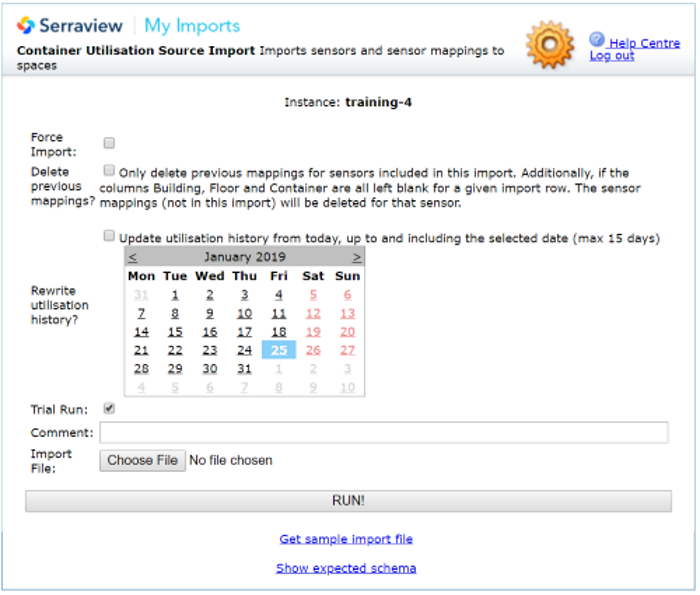
- Navigate to Admin Settings > Data Imports > Data Imports.
- Click the Container utilisation source mapping import link.
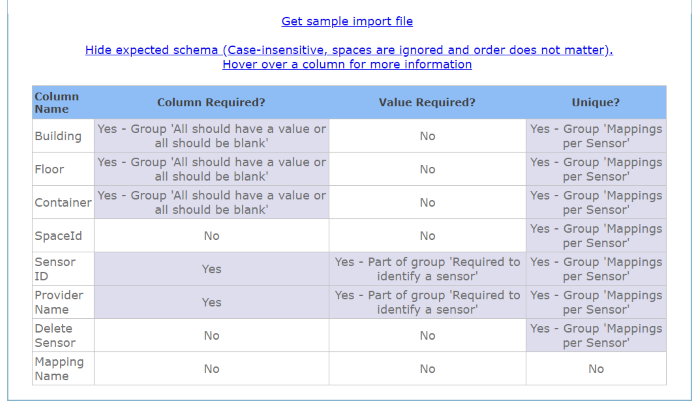
3. Click the Show Expected Schema link to view the columns.
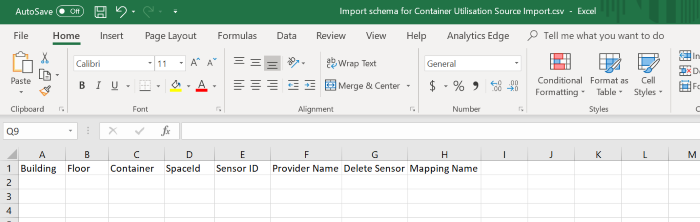
4. Click the Get sample import file link to download the Import schema for Container Utilisation Source Import.csv file.
5. Open the Import schema for Container Utilisation Source Import.csv file.
6. Complete the import file from the import schema with the following values. All other fields can be left blank.
The table below describes the columns.
|
Column |
Value |
|---|---|
|
Building |
This is the building name in Serraview, and this is used to identify the building. |
|
Floor |
This is the floor name or number in Serraview, and this is used to identify the floor. |
|
Container |
This is the floor name in Serraview (same as above). |
|
Sensor ID |
This is the ID number obtained from Step 1. Obtain Mappings. |
|
Provider Name |
This is the provider's name either Aruba AirWave or Cisco. |
7. Save the import file with a relevant filename.
8. Upload the import file, refer to the Trial Run Imports.
Validate the Mappings
You can check the mappings in the 339 SVLive Utilization Source Container Mapping Report. This report shows whether a source has been mapped to a building and floor.
339 SVLive Utilization Source Container Mapping Report
This report shows whether a source has been mapped to a building and floor.
Key Data
- Building
- Floor
- Container
- Utilisation ProviderID
- Utilisation Provider Name
To view and run this report, your user account will need the report's secured actions, refer to Security in Reporting.
If you require access, then contact your System Administrator. For information on how to add secured actions to a role, refer to Manage User Roles.