- What is SCIM?
SCIM, or System for Cross-domain Identity Management specification, is an open standard designed to manage user identity information. The goal of SCIM is to securely automate the exchange of user identity data between identity providers and service providers requiring user identity information (such as enterprise SaaS apps).
SCIM provides a defined schema for representing users and groups, and a RESTful API to run CRUD (create, read, update, delete) operations on those user and group resources.
- Why use SCIM?
Maintaining identities across multiple platforms can be time-consuming, labor-intensive, and prone to inconsistencies and error. SCIM streamlines these processes and reduces mistakes. It enables systems to communicate with each other in near-to-real time, ensuring user data is consistent across all platforms.
- When should we use the SCIM API?
Our SCIM API is designed for businesses who want to manage their user identity in cloud-based applications and services and require enhanced interoperability, security, and scalability. If you have Azure Active Directory or other SCIM compatible identity management system, building connections to our SCIM API is a straightforward approach.
The technical prerequisites to use our SCIM API are:
- SCIM-compliant Identity Providers / API service.
- The latest cloud version of Eptura Engage.
- Cloud customers only
- How does SCIM make provisioning easier?
The standard user object schema and RESTful APIs for management defined in SCIM 2.0 allow Identity Providers and apps to integrate more easily. Application developers can use our SCIM endpoints to integrate with any SCIM-compliant client.
- What does Eptura Engage provide?
Eptura Engage provides access to our SCIM API documentation and API endpoints. Your application experts will develop and configure the Identity Management System and the connection with our SCIM API. We have created detailed guidance on the format of the request and the responses you can expect when integrating with Eptura Engage.
- What is the difference between the SCIM API and HR Feed?
HR Feed uses a configurable Windows Application to GET User data from Microsoft Active Directory only and does not support Identity Management Systems such as Azure Active Directory or Okta.
Our SCIM endpoints allow any SCIM compatible Identity Management System to push user data to Eptura Engage.
- Does on-premises Active Directory work with SCIM API?
No, on-premises Active Directory does not work with SCIM API.
- What version of SCIM do you support?
SCIM v2.0
- Which type of user is created via the SCIM API?
By default, a Form user is created. All users are created as standard, non-admin users.
- Can the default location for a user be set?
Yes, the default location and country can be set via the SCIM API.
- What is the lifetime range of SCIM token generated via the token provider?
The minimum and maximum valid value range for expiry is 1 minute to 10 years. Values beyond this range trigger a 400 BAD REQUEST. If ‘tokenexpiry’ is not provided in the request, it is set to 24 hours by default.
- What is the ‘ExternalId’ user attribute?
ExternalId is a unique user attribute in your SCIM Identity provider. For an SSO user, ‘ExternalId’ is usually a GUID, for example for Azure AD, it will be similar to ‘111Cxxxx-xxxx-xxxx-xxxx-11111111xxxx’. For a Form user, it can be anything alphanumeric, e.g. ‘Externaluser123’
- When a user is permanently deleted are their room and desk bookings also deleted?
All room bookings where the deleted user is the host are deleted. If the deleted user created a booking but is not the host, the booking is not deleted. All desk bookings for the deleted user are deleted, regardless of who created them. An email notification with details of the deleted bookings is sent to the administrator.
- Who is notified when a user is permanently deleted from SCIM?
By default, notifications regarding users deleted from SCIM are sent by email to the first admin user created. To divert the notification to a different mailbox, add the desired destination email address to the tenant setting ‘EmailTargetUserId’
- Can a SCIM client be set up to work with two Eptura Engage deployments?
No.
- Can a Eptura Engage deployment be set up to accept user imports from two SCIM clients?
No.
- Is Eptura Engage SCIM API a 2-way synchronization of users?
No. Eptura Engage SCIM API is never triggered from within Eptura Engage. Only the SCIM client.
- When a user is deactivated and then reactivated, does the user start functioning again in Eptura Engage?
Yes. However, the user cannot be recovered if the user is deleted via SCIM API.
- How frequently does Eptura Engage receive changes via SCIM API?
The period between synchronization and calculating changes in data is entirely dependent on the SCIM client. The client is responsible for reading the current user data by using the GET endpoints. Alternatively, it can save the last sync state and then decide what changes to communicate.
- What permissions or secret details are communicated to Eptura Engage by Azure AD?
No Azure AD permission or secret details are communicated to the Eptura Engage SCIM API. The customer’s domain name is needed for verification purposes.
- Can I change the field mappings of the supported SCIM fields with those of the Eptura Engage fields?
No. However, the client can change the mapping between their Identity Provider and supported SCIM standard fields. Handling this conversion is the responsibility of the SCIM client.
- Can multiple OUs (Organisational Units) be configured or filtered for SCIM?
No, SCIM does not support OUs therefore no OU information is passed to the Eptura Engage SCIM API. However, if your own SCIM compatible client supports it (Azure AD does not) you can filter using your own client before passing the information across.
- How frequently must my access token be refreshed?
You can choose a short expiry for tokens (minimum is 1 minute but a few hours is recommended) and periodically generate a new token. If your SCIM compatible client cannot create a token (Azure AD for example, cannot create tokens), you can generate a long expiry period (10 years maximum) using the Eptura Engage API. However, your system administrator will need to refresh the token when it expires.
- What is the ‘ExternalId’ group attribute?
‘ExternalId’ is a unique group attribute in your SCIM Identity provider. It cannot be updated. It can be alphanumeric, e.g. ‘Externalgroup123, or GUID, e.g. ‘111Cxxxx-xxxx-xxxx-xxxx-11111111xxxx’.
- How do you check the group membership of a user?
Use ‘Get Group’ by filter with ‘userId’ to return the group a user is a member of.
- Can ‘Get Group’ endpoint return the entire member list?
No, the ‘Get group’ endpoint does not return the entire member list.
- What filters are supported by the ‘Get Group’ filter endpoint?
The following group attributes are supported by the ‘Get Group’ filter endpoint: ‘groupName’, ‘externalId’, ‘members’, and ‘groupid’.
- What filter operators are supported by the ‘Get Group’ filter endpoint?
The following filter operators are supported by the ‘Get Group’ filter endpoints (operator command in brackets): equals (eq), contains (co), starts with (sw), ends with (ew), and not equals (ne). However, the ‘members’ and ‘groupId’ group attributes support only the equals (eq) operator.
- What filters are supported by the ‘Get User’ filter endpoint?
The following user attributes are supported by the ‘Get user’ filter endpoint: ‘userName’, ‘firstName’, ‘lastName’, ‘email’, ‘telephone’, ‘mobile’, ‘externalId’, and ‘accountactive’.
- What filter operators are supported by the ‘Get User’ filter endpoint?
The following filter operators are supported by the ‘Get User’ filter endpoints (operator command in brackets): equals (eq), contains (co), starts with (sw), ends with (ew), and not equals (ne). However, the ‘accountactive’ user attribute supports only the equals (eq) operator.
- What users are returned when ‘Get User’ endpoint is called with no filter?
Only the active users created/merged from SCIM and of the same user type defined in the SCIM client. By default, the tenant setting ‘userType’ is set to Forms users.
- Can I delete a user created in the Eptura Engage web application?
No. You can only delete users created/merged from SCIM and those of the same user type defined as ‘userType’ tenant setting in the SCIM client. By default, the tenant setting ‘userType’ is set to Forms users.
- Why can’t I can’t see the ‘External groups mapping’ menu item in the Eptura Engage web application?
Check the option is enabled. Navigate to Advanced setup > Global setup and on the Application tab, scroll down to Menu Options and set External groups mapping to ‘True’. If External groups mapping is still not visible in the Advanced setup menu, contact Eptura Support.
- We have existing users in Eptura Engage. Can we perform user operations for our existing users via SCIM API immediately after onboarding to SCIM?
No, you must follow the migration path for existing users first. Learn more about migrating existing users
- Can the userName attribute for a user be updated through SCIM?
SCIM can update the user attribute if the userName does not already exist in Eptura Engage.
- What is the ExternalId value for Okta users in SCIM?
Okta user identifier is the ExternalId value in SCIM.
- What is the ExternalId value for Okta groups in SCIM?
Okta group name is the ExternalId value in SCIM.
- Does SCIM support multiple IdPs?
Yes, SCIM supports multiple IdPs (Azure AD only) for Eptura Engage customers who have one Eptura Engage instance and more than one Azure AD tenant. See notes below.
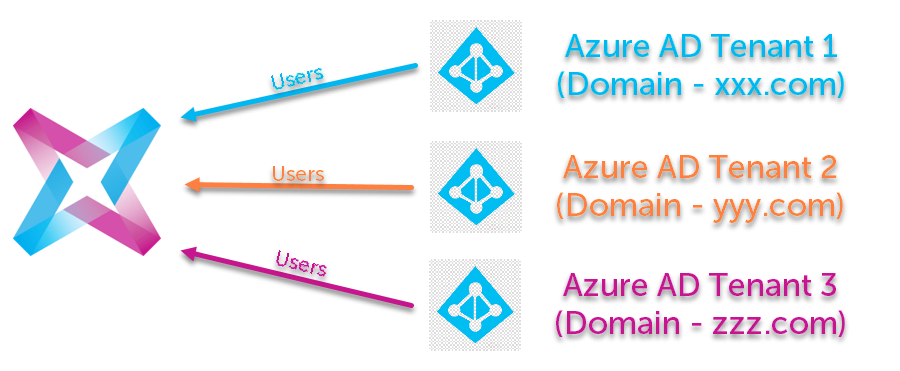
Requirements and notes for multiple IdPs:
- Users from multiple IdPs can be imported to one Eptura Engage instance only.
- All users from each Azure AD tenant are imported.
- Onboarding is only required once. The same SCIMClientID and SCIMSecret are used for all Azure AD tenants.
- After onboarding, SCIM applications must be configured with the same SCIM token on all Azure AD tenants. (SCIM token is generated from the SCIM token API).
- SSO configuration in Eptura Engage must be updated with the multiple IdP metadata configurations.
Learn how to configure Eptura Engage SSO with multiple IdPs
When the users from all Azure AD tenants are provisioned into Eptura Engage, users can sign in to Eptura Engage.

