Microsoft 365 service account
How to create a Microsoft 365 service account for Eptura Engage
- Login to Microsoft 365 Admin center with your Microsoft 365 admin account.
- Click Add user from User management.
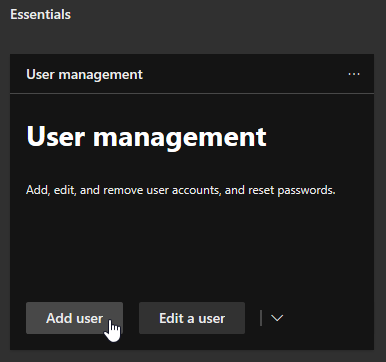
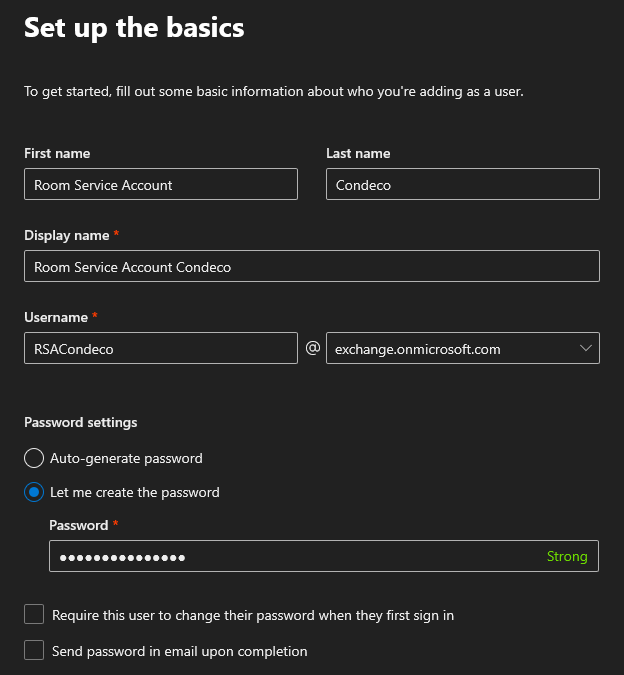
- Complete the form for your service account and create a password.
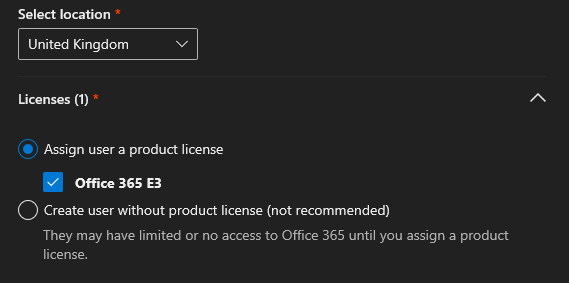
- The Service Account will need at least an ‘E1 license’
- Click Add to create the service account.
The service account must be set to never expire!
Apply impersonation rights
Impersonation is mandatory for Exchange Sync. It is used by the Microsoft 365 service account to create bookings in room calendars.
Impersonation allows the service account to send event notifications ‘from’ the room mailboxes in order to manage events regardless of who originally created them.
We recommend using Management Scope restricting the service account impersonation access for the required rooms only. Learn more about controlling access to calendars
Impersonation rights can be applied with the following PowerShell script:
New-ManagementRoleAssignment -name: <Impersonation Name> -Role:ApplicationImpersonation -User: <service account smtp address>
Learn more about configuring impersonation rights, at Microsoft:
https://docs.microsoft.com/en-us/exchange/client-developer/exchange-web-services/how-to-configure-impersonation.
Permissions granted to the service account
During the Exchange Sync setup process, you will authorize the following permissions to the service account:
| Permission required | Description | Type | Reason |
|---|---|---|---|
| Calendars.ReadWrite.All | Read and write calendars in all mailboxes. | Application | Required to read and update events of calendars without a signed-in user. |
| EWS.AccessAsUser.All | Access mailboxes as the signed-in user via Exchange Web Services | Delegated | Required by the service account configured with the impersonation rights, to allow it access to mailboxes on behalf of users. Note: This permission is only available to the service account when “Authorize via service account” is clicked during the Microsoft 365 Sync setup process. |
| User.Read | Sign in and read users profile. | Delegated | Required to allow AAD user to login. |
