User Provisioning Overview
Part of hiring new employees is provisioning the applications they need to do their jobs and then, during their time at your company, ensuring security and user accounts are up to date. When they leave your company, their access needs to be quickly revoked from the applications. User Provisioning is an identity management process that ensures user accounts are created, given proper permissions, changed, disabled, and deleted.

Using SCIM instead of manually managing this process is less time-consuming and more accurate, as a manual process is more error-prone. SCIM streamlines these processes and reduces mistakes. It enables systems to communicate with each other in near-to-real time, ensuring user data is consistent across all platforms.
SCIM Overview
System for Cross-domain Identity Management (SCIM) is an open standard for a set of API endpoints that enable automation of user provisioning. The goal of SCIM is to securely automate the exchange of user identity data between identity providers and service providers requiring user identity information (such as enterprise SaaS apps). SCIM provides a defined schema for representing users and groups, and a RESTful API to run CRUD (create, read, update, delete) operations on those user and group resources.
Eptura’s SCIM-compliant API enables communication with SCIM-compatible systems providing user identity information. The Eptura SCIM API uses the SCIM 2.0 protocol, which provides a defined schema for representing users and groups, and a RESTful API to run CRUD operations on those users and groups.
SCIM provides a defined schema for representing users and a RESTful API to update the database for those users. Also, you can set up the SSO Identity Provider (IdP) to synchronize passwords to ensure that a user’s IdP password and the User Provisioning password match.
Additionally, user profile attributes can be mapped user attributes from the source application (Eptura) and the User Provisioning Service user profile. The SCIM Integrations listed below have been enhanced to support user-defined custom attributes, which will enable the User Provisioning Service to import the attributes into Eptura.
To find out more about the SCIM defined schema, see System for Cross-domain Identity Management: Core Schema.
The integrations we have available are:
Eptura SCIM API
The Eptura SCIM API is designed for businesses who want to manage their user identity in cloud-based applications and services and require enhanced interoperability, security, and scalability.
The prerequisites to use our SCIM API is:
- To have an SCIM-compliant Identity Provider / API service. The standard user object schema and RESTful APIs for management defined in SCIM 2.0 allow Identity Providers and apps to integrate more easily. Application developers can use our SCIM endpoints to integrate with any SCIM-compliant client.
- A SCIM-API valid bearer access token, generated and provided by Eptura.
Eptura provides access to our SCIM API documentation and API endpoints. Your application experts will develop and configure the Identity Management System and the connection with our SCIM API. Learn more in Eptura SCIM API Developers Guide.
Technical Explanation
Eptura SCIM is designed to exchange user/group information created at the client’s Identity provider to Eptura and then publish the information to a message broker so the downstream Eptura modules can consume the users/group data.
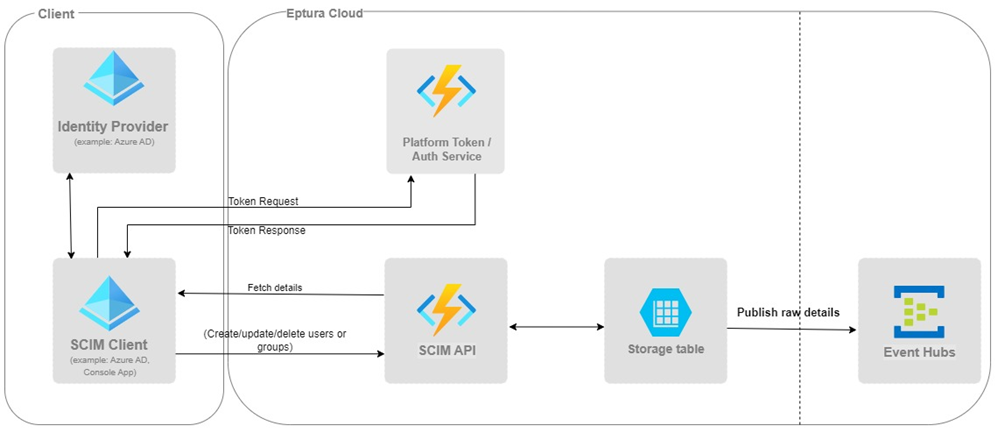
The table below describes what is supported and the limitations.
| Supported | Limitations |
|---|---|
|
The following actions are supported:
|
The Eptura SCIM API has the following limitations:
|
